IT Systems & Security Audit and assurance services provided to evalaute:
- IT performance
- Internal Controls of the system
- Compliance with external requirements (laws, regulationns and agreements)
- Evaluation of the governance structure of the IT system
Assessment of effectiveness of IT systems will cover all the major controls:
- Logical Access
- Data Protection
- Input
- Processing
- Output
- Interface
- Change Management
- Contingency Planning and Backup
- System Scalability
Information Systems Audit
An information system (IS) audit or information technology(IT) audit is an examination of the controls within an entity's Information technology infrastructure. These reviews may be performed in conjunction with a financial statement audit, internal audit, or other form of attestation engagement. It is the process of collecting and evaluating evidence of an organization's information systems, practices, and operations. Obtained evidence evaluation can ensure whether the organization's information systems safeguard assets, maintains data integrity, and are operating effectively and efficiently to achieve the organization's goals or objectives.
An IS audit focus on determining risks that are relevant to information assets, and in assessing controls in order to reduce or mitigate these risks. An IT audit may take the form of a "general control review" or an "specific control review". Regarding the protection of information assets, one purpose of an IS audit is to review and evaluate an organization's information system's availability, confidentiality, and integrity by answering the following questions:
- Will the organization's computerized systems be available for the business at all times when required? (Availability)
- Will the information in the systems be disclosed only to authorized users? (Confidentiality)
- Will the information provided by the system always be accurate, reliable, and timely? (Integrity).
The performance of an IS Audit covers several facets of the financial and organizational functions of our Clients. The diagram below gives you an overview of the Information Systems Audit flow: From Financial Statements to the Control Environment and Information Systems Platforms.
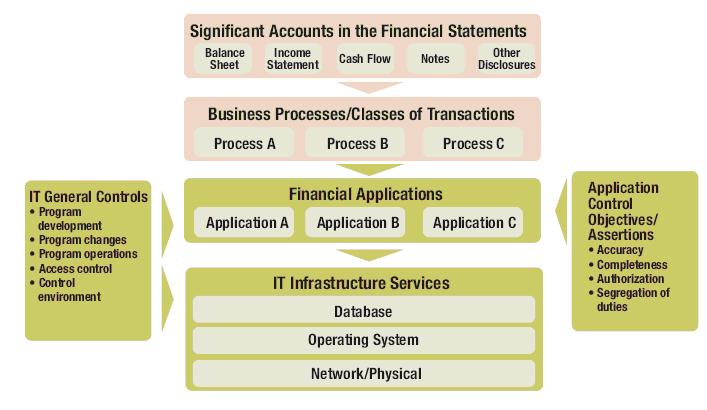
Audit Refernce Framework:
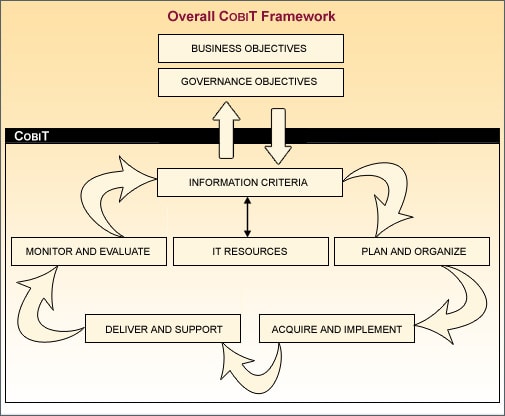
Success of audit depends not only upon the auditors expertise but also on the reference framework used in order to ensure comprehensive compliance and risk reduction. A suitable refernece framework will be chosen based on the best Internatioanl practices such as COBIT.
COBIT is a governance framework and supporting tool set that IT organizations can use to ensure that IT is working as effectively as possible to minimize risk and maximize the benefits of technology investments.
The COBIT control framework links IT initiatives to the business requirements, organizes IT activities into a generally accepted process model, identifies the major IT resources to be leveraged and defines the management control objectives to be considered.
Risk based Audit Strategy
Identifying risks and vulnerabilities allows the auditor to determine the controls needed to mitigate those risks. In a risk-based audit approach, IS auditors are not just relying on risk. You are also relying on internal and operational controls, as well as knowledge of the organization. This type of risk assessment decision can help relate the cost-benefit analysis of the control to the known risk, allowing for practical choices and better cost-benefit recommendations to management.
Knowledge of the relationship between risk and control is important for IS auditors. IS auditor will
- Differentiate types of risks related to business, technology and audit
- Identify relevant controls to mitigate these risks
- Evaluate the organization's risk assessment and management techniques
- Assess risk in order to plan audit work
Profiles of significant business units, departments and products, including:
- Data
- Applications and operating systems
- Technology
- Facilities
- Personnel
And associated business risks and control features will be included as a part of audit.
And associated business risks and control features will be included as a part of audit.
- Conduct inherent risk assessment
- Conduct detection risk assessment
- Perform tests on reliability and risk prevention
- Perform substantive audit procedures
- Create recommendations
Approach
Audit Preparation
- Discussion with the IT team and the SPOC for getting handhold of the Kosharu system
- Discussion with the Risk Management team to know the current status
- Discussion with the relevant team to know the compliance requirements
- Discussion with the BCP team
- Obtain and study the Process Flow Documents
- Prepration and getting approval of audit templates
Onsitee Audit phase
- Assessment of the current status of Risks present in the IT system in meeting the objectives.
- Test of Design: Whether the controls have been designed to mitigate the risks identified. Samples will be selected and assessed for each of the identified processes.
- Test of Design: Whether the controls have been designed to mitigate the risks identified. Samples will be selected and assessed for each of the identified processes.
- Test of Effectiveness: Are the controls functioning as designed and continue to meet the control objectives? Required number of samples for each of the controls to be tested will be selected and tested. The sample size will be decided based on the frequency of the controls and the size of the population.
- Relevant evidences will be obtained and workpapers will be compiled. Further, rough draft of the audited proceedings will be prepared and discussed with the auditees and the responses will be recorded.
- This is expected to take three weeks and will be conducted at the MPAO at the relevant sites where the respective processing happens.
Audit Report preparation:
- Preparation of the audit report and Key Audit Findings along with the recommendations for improvement along with the annexures and workpapers.
- This is to be conducted off-site after completing the assessment at site locations.
.jpg)
Audit Preparation
- Discussion with the IT team and the SPOC for getting handhold of the Kosharu system
- Discussion with the Risk Management team to know the current status
- Discussion with the relevant team to know the compliance requirements
- Discussion with the BCP team
- Obtain and study the Process Flow Documents
- Prepration and getting approval of audit templates
Onsitee Audit phase
- Assessment of the current status of Risks present in the IT system in meeting the objectives.
- Test of Design: Whether the controls have been designed to mitigate the risks identified. Samples will be selected and assessed for each of the identified processes.
- Test of Design: Whether the controls have been designed to mitigate the risks identified. Samples will be selected and assessed for each of the identified processes.
- Test of Effectiveness: Are the controls functioning as designed and continue to meet the control objectives? Required number of samples for each of the controls to be tested will be selected and tested. The sample size will be decided based on the frequency of the controls and the size of the population.
- Relevant evidences will be obtained and workpapers will be compiled. Further, rough draft of the audited proceedings will be prepared and discussed with the auditees and the responses will be recorded.
- This is expected to take three weeks and will be conducted at the MPAO at the relevant sites where the respective processing happens.
Audit Report preparation:
- Preparation of the audit report and Key Audit Findings along with the recommendations for improvement along with the annexures and workpapers.
- This is to be conducted off-site after completing the assessment at site locations.
.jpg)
